A few months ago, John Smith received a voucher for a fancy dinner for two. The voucher had been given to him as a gift. To use it, he needed to first activate it on the issuing company’s website:
 As he was entering the voucher number, he noticed that the moment he entered the last digit, a small green V appeared next to the number, validating the voucher number. If he added an incorrect digit or removed a correct one, the green V would change to a red X.
As he was entering the voucher number, he noticed that the moment he entered the last digit, a small green V appeared next to the number, validating the voucher number. If he added an incorrect digit or removed a correct one, the green V would change to a red X.
It wasn’t long before John discovered that the web page was constantly sending the voucher number to the server, and receiving a “Good” or “Bad” response for each character as it was attempted. To make matters worse, this action had no limitations and could be repeated any number of times, effectively allowing an attacker to swiftly find each number in the code because typically there is no rate limit or not attempt count limit, and thus brute-force their way to whatever the voucher was worth. It wouldn’t even require user credentials to gain access.
This is one example of how some coupon issuers make it too easy for hackers. This real-life incident could be exploited by a single hacker but bots are easily programmed to take advantage of such a vulnerability on a large scale.
Online coupons have several qualities that are very attractive to hackers:
- Money is within easy reach—once a hacker obtains the code, it is fungible; meaning they can sell it easily.
- They are easily crackable.
- The actual owner of the money probably won’t be alerted that money is being siphoned from his or her gift card and may never figure it out. The hacker is gone long before discovery.

Inbar Raz, principal researcher, PerimeterX
And if that weren’t bad enough, John also discovered that the voucher numbers were created in a certain format that significantly reduced the number of possibilities to scan through. In fact, it took less than 100 attempts to guess another valid voucher number.
Luckily for the voucher issuer, John Smith happened to be a researcher at a security company, and he promptly warned the online retailer that it was completely exposed. But those, who go hunting for such vulnerabilities, are often not as kind. A recent study from Tripwire suggests, criminals aim to crack coupon and voucher codes, as well as gift card numbers, on a large scale. Hackers can acquire coupon and giftcard numbers from the issuers, merchant, reward redemption program, etc through various methods, including phishing, SQL injection, social engineering and accidental disclosure. When they succeed, they either use the codes or resell them on the black market. While the act of trying to brute-force login credentials (known as Account Takeover, or ATO) is frequently mentioned in the media, there is rarely any mention of brute-force attempts on coupon, voucher and gift card codes.
Who is hurt by this automated fraud – and how badly?
When coupons and vouchers are given to a customer, that person might choose not to use them immediately, but rather save them for a later day. Maybe a birthday or an anniversary, maybe a visit to a remote city. If the coupon or voucher is discovered by hackers and someone else uses it, two things happen:
- The hackers use the voucher and claim the product or the discount, or sell them on the black market.
- The real customer discovers that their voucher is not working. To keep a loyal customer, the retailer has to either reissue the voucher, or compensate the customer, at an even bigger cost.
What can retailers do?
Online retailers should to take a number of precautions, or they are simply inviting the fox into the henhouse. Here are straightforward safeguards for every company putting coupons and gift cards online. Retailers who implement them have a fighting chance to protect their customers and themselves.
Don’t trust the browser
Some coupons, particularly seasonal ones, are offered to customers on the condition that they agree to do something. Commonly, this could be signing up to a mailing list. Once the customer enters the requested information, the coupon code is revealed.
We’ve seen retailers send out the coupon code in the original HTML page, hidden from view, only to be revealed at the end of the process:
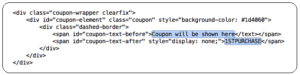
As you can see, by sheer inspection of the downloaded HTML, the coupon code can be extracted. The code should only be sent to the user side, however, after the server has verified that the user had entered the requested information.
Create generic and personalized coupons
Make part of the coupons generic, so everyone can use and share them. Those coupons serve the purpose of generating traffic back to your website because customers can share these reusable coupon codes widely and customers are more likely to shop on websites they can use coupons for versus the one they do not. Additionally, according to a recent survey. 85% of consumers search for coupons before visiting a retailer’s site. The rest should be personalized and unique, so only those loyal customers you intend to have them, will actually receive them.
Create coupon codes that are complex and hard to guess
Many retailers choose codes that are easy to guess. Commonly, they will be made up of a word, followed by a number (often representing the discount percentage). A few examples:
1STPURCHASE, JUSTGO, XMASEBOOK, SECRET50, BOOK20, BUNDLE10, SUCCESS10, PROMO20
Online coupons should be random and contain both letters and numbers, to be immune to common or automated guessing.
A couple of examples for well-constructed coupon codes:
6ZWTL35R74A4VQQPMOY6, D73JO1N8KEQG
While the above coupon codes are not easy to type into a website form, a customer will not be turned off by such a long coupon code because most retailers send confirmation emails with coupon codes allowing customers to simply copy and paste the code into the online form. This method not only makes it easier for customers to receive discounts, it also negates malicious bot attacks.
Attach a validity period to each coupon
Online coupons should have a limited validity. “Not valid before …” and “Not valid after…” will solve the problem of an unexpected (or uncontrolled) use rate of the coupons. This is particularly important, if a large amount of coupons is generated beforehand, or if the vendor wishes to limit or control the rate of use.
Validation and enforcement
Verify all the details, such as the coupon number or PIN code, and make sure the coupon is used within the applicable terms and conditions.
Also, retailers should require an additional piece of information , that is much harder to guess, such as email address or a phone number of the gift card recipients in conjunction with the card data itself.
Restrict online balance checks
Online balance checks should require some form of strong authentication. The coupon/voucher/gift card number alone should not give a hacker access and control. There should be another authentication factor, such as a PIN code (although criminals have found ways to beat that as well). Adding a CAPTCHA is also helpful in the effort to prevent automated checks of card balance.
And when possible, a pre-registration and login should be required.
Use a web behavior-based approach to protect from online fraud
In order to protect your customers and your business, use a behavior-based approach, like monitoring how users interact with your website by observing the mouse movements or the click speed, to detect and block automated attacks. This requires a technology which can distinguish human activity from malicious bot activities.
Attacks on retail websites are not merely commonplace, they are constant. Automation and more sophisticated bots have made these attacks harder to detect and potentially more damaging to a retailer’s business, impacting customer loyalty and brand reputation. This means retailers should not delay deployment of up-to-date bot protection, in addition to taking common-sense precautions that make life at least somewhat challenging for hackers.
PerimeterX specializes in detecting and mitigating automated web attacks.