As companies enter new markets and add new forms of digital payment, fraudsters and hackers often see more opportunities for disruption. With risk of data theft and fraud loss on the rise, data security and fraud management have become high-priority executive concerns.
The high stakes of data protection and fraud management
Executives say maintaining trust in a digitized society is increasingly difficult, in part because of the vast amount of sensitive information vulnerable to hackers. A security breach that exposes sensitive personal information is the top unintentional action that’s toxic to a company’s reputation, according to CGMA Magazine.
In addition to tarnished brand identity, data breaches impact stock value and cost large sums of money. Stock prices fall an average of 5% after a data breach is disclosed, and the average total cost of a data breach is $3.62 million, according to the Ponemon Institute’s 2017 Cost of Data Breach Study.
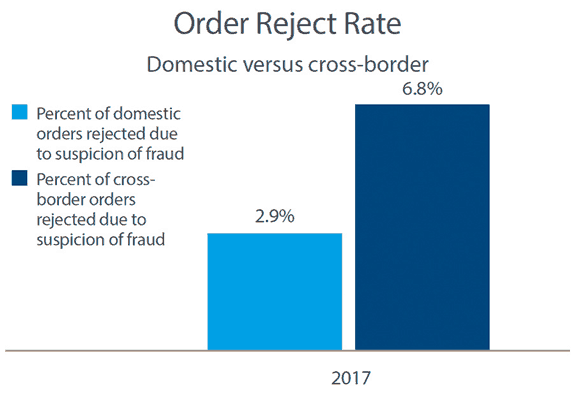
As digital payments increase, fraud management also becomes a higher priority. The average fraud loss for online purchases is 0.99%, and for mobile transactions it’s 0.89%, compared to just 0.3% for phone or mail order, according to the CyberSource 2017 Online Fraud Benchmark Report.
To minimize fraud loss, streamline fraud management operations and maximize revenue, it’s important to track fraud separately for each channel, and to use efficient automated screening to minimize the number of genuine transactions that require review.
Minimize fraud loss and security breaches through sophisticated risk mitigation strategies
Today’s digital economy requires a holistic way to manage fraud that’s more thorough than the traditional approach of relying only on screening and manual review. This four-phase approach begins by reducing the threat of fraud when the customer first establishes an account and continues all the way through to the moment a transaction is approved. Each of these four crucial phases—account monitoring, automated screening, authentication and review—features specific challenges that require specific solutions. Learn more about the four key phases and how to make sure you’re addressing each one by reading our guide, The Four-Phase Approach: A More Effective Way to Manage Fraud.
To secure customer payment data without over-complicating payment experiences, it’s important to have a clear understanding of payment security. While that may sound easy, there are many misconceptions about payment security goals, the most effective strategies, and even the types of organizations that are most at risk. Two of the most common myths that hinder companies’ security capabilities are that hackers only target large companies and that you need raw payment data to run your business. Read our e-book, The Five Myths of Payment Security, to debunk the most common misconceptions.
For more insights on maintaining effective fraud management and payment security while creating new customer experiences, visit our resource hub, Ready for Next.
Favorite